May 2009
Examining the Impact of Market Size on Facility Security Operations at Indoor Multipurpose Facilities on College and University Campuses
- George N. Smith, Clemson University
- Benjamin D. Goss, Missouri State University
- Colby B. Jubenville, Middle Tennessee State University
The scope of security issues at public assembly events has become more complex and expensive as perceived threat levels, significance, and size of major events increase, causing them to become plum target[s] for terrorists and require exponential increases in costs. (Petrecca, 2003).
While the U.S. Government’s annual budget for domestic security has increased 64 percent since 2002, no federal funds are available for privately operated stadia and arenas. Additionally, although stadium security has become a top priority on college campuses since September 11, 2001, state budget shortfalls frequently prevent sizeable investments in similar public college and university building security (Kennedy, 2001).
Poor training and performance by event staff, increasing incidents of spontaneous terror at public assembly events, and new organized terror security threats (which are growing in their sophistication, unpredictability, and probability of mass destruction) have increased the urgency for the facility management industry to review and upgrade security protocols to ensure that multi-purpose arenas and stadia have the safest environments possible (Merideth, 2002; Goss, Jubenville, & MacBeth, 2003). Consequently, expectations for facility managers’ performance on security matters have increased dramatically (Hancock, 2002).
The purpose of this study was to determine if applications of best security practices, as identified in the IAAM Safety/Security Best Practices Planning Guide for Stadiums/Arenas/Amphitheaters, are significantly different in major market locations versus secondary market locations. Quantitative data were collected from professionals in the field of facility management regarding the security practices currently in place at venues in which they work to determine any differences in application. As the significance and size of public assembly events increase, so does the complexity of security for these events. Also, patron safety continues to be of paramount concern to facility managers at any event in their venues, regardless of the event’s scope and significance. Since the terrorist attacks of September 11, 2001, the primary focus of security experts in the public assembly industry has focused upon preventing acts of organized terror in public assembly venues.
Professional assembly and event organizations such as the International Associations of Assembly Managers (IAAM) have led efforts to create professional standards on security matters, including best-practice planning guides distributed through IAAM’s Center for Venue Management Studies.
Regardless of the size or significance of an event in a public assembly facility, the most urgent concern of facility managers is to ensure no harm comes to the event attendees (Rowe, 1993). The general rule of law for the past 50 years has been that fans assume inherent risk of the dangers normally associated with any sporting event they attend, such as foul balls at baseball games (“Sports Violence,” 2001). However, in post-modern legal consideration, patrons and guests who attend events at public assembly venues are considered business invitees, and, as such, venue management has the legal responsibilities to inform invitees of known and unknown risks, inspect facilities for potential safety threats, keep facilities well maintained and in good repair, and, above all else, keep people in and around the premises safe. Failures by venue managers to take actions against foreseeable criminal action and to make their venues safe increase liabilities of venues and even individual staff members (Fried, 1998).
However, budget and time constraints frequently dictate actual implementations of these “best practices” in the field. Additionally, the ability of the marketplace in which facilities are located, along with the perceived threat level of that market, often determine each facility’s ability to bear or pass on the cost of additional security, given no federal monies are available for private stadium or arena security.
Poor training and performance by event staff, progressively increasing incidents of spontaneous fan violence at public assembly events and new organized security threats, growing in their sophistication, unpredictability and probability of mass destruction, have increased the urgency for the facility management industry to review and upgrade security protocols to ensure multi-purpose arenas and stadia have the safest environment possible (Meredith, 2002). As a result, expectations for the training and performance of facility managers on matters relating to security have increased dramatically (Hancock, 2002).
Professional associations such as the International Association of Assembly Managers (IAAM) have led massive efforts to create standard professional methods for training staff and developing security procedures that better ensure the safety of fans, staff, and artists while simultaneously limiting venue liability. Soon after September 11, 2001, IAAM created a Safety and Security Task Force (SSTF) that developed a series of “best practices” to assist facility managers plan and implement security programs at their venues. Distributed through IAAM’s Center for Venue Management Studies, the series’ topics include:
- Safety/Security Best Practice Planning Guide for Stadiums/Arenas/Amphitheaters
- Safety/Security Best Planning Guide for Convention Centers/Exhibit Halls
- Safety/Security Best Practice Planning Guides for Theaters and Performing Arts Facilities
- Safety /Security Best Practices Planning Guide for Emergency Preparedness
Through various audio and internet conference calls, the SSTF has presented this information to more than 2,000 people since early 2002 (Herrick, 2003). Users of the guides complete checklists to determine which specific venue and security practices they should implement relative to specific criteria listed in the guides (Herrick, 2002).
However, budget and time constraints again continue to be a limiting factor in the implementations of many of these best practices. Consequently, these new training programs are rarely comprehensive in their approaches (Baugus, 2001). Therefore, while the best practices related to safety and security are being identified by industry professionals and related professional organizations, their specific practical uses in the field need further examination.
The purpose of this study is to determine if applications of best security practices, as identified in the IAAM Safety/Security Best Practices Planning Guide for Stadiums/Arenas/Amphitheaters, are significantly different in major market locations versus secondary market locations. Quantitative data were collected from professionals in the field of facility management regarding the security practices currently in place at the venues in which they work to determine their difference in application, if any.
Terror: The Threats
The nature of the September 11 attacks demonstrated the existence of terrorists who would also consider similar larger scale attacks on arenas or stadia (Palumbo, 2003). Consequently, government officials and leaders within the public assembly management industry have taken action to tighten security in publicly trafficked areas throughout the country and create environments at public assembly venues that make patrons feel more safe, secure and comfortable, thereby making the public assembly industry viable economically (Rowe, 1993).
Spontaneous Terror
Prior to terrorist attacks on September 11, 2001, public assembly venue security dealt primarily with rowdy fans, medical emergencies, purse thefts, and other routine occurrences associated with large crowds, including slightly larger-scale disturbances called spontaneous terror attacks (Elrick, 2002; Goss, Jubenville, & MacBeth, 2003) a rising concern of facility managers because of its increasing commonality in which fans engage in sudden, unpremeditated violent outbursts (Goss et al., 2003), as illustrated in the following four examples. In September 1999, a fan jumped from the stands and tackled Houston Astros outfielder Bill Spiers during a game at Milwaukee’s County Stadium. In May 2000, at a professional baseball game between the Chicago Cubs and Los Angeles Dodgers at Wrigley Field in Chicago, Illinois, a fan struck a Dodgers player sitting in the bullpen and stole his cap. Several Dodgers players then jumped into the seating area and began fighting with fans (“Previous Examples,” 2002). During a July 2003 Oakland Athletics baseball game, a fan threw a firecracker from the top deck of Oakland/Alameda County stadium into the lower bleacher seats, burning the legs of an eight-year-old boy (“Tossed Cherry,” 2003).
Market size notwithstanding, in November 2002, after the homestanding Clemson Tigers football team defeated their arch-rival South Carolina Gamecocks, celebrating Clemson fans 37 stormed onto the field and tore down a goal post, literally trampling a security guard who was left with broken ribs, a broken collar bone and a heel imprint on his forehead (Romano, 2002). One season later, Clemson University athletics officials reacted with an aggressive plan labeled as the “Gathering at the Paw” initiative, which established a new tradition in which fans would gather at the Tiger paw painted at midfield to celebrate wins and interact with the players after the game. However, this plan failed to prevent a reoccurrence of this incident one year later, as moments after Clemson upset third-ranked Florida State University in November 2003, Clemson fans again stormed the field and leveled a goal post in a scene very similar to the 2002 South Carolina game.
Organized Terror
While fans are more likely to be injured or hurt as the result of a spontaneous terror incident (Goss et al., 2003), the security threat requiring the most proactive approach, threatening the most serious consequences, and requiring the primary focus of security consultants in the public assembly industry are acts of organized terror (Palumbo, 2003), as detailed in the following examples. In the summer of 2003, two female suicide bombers killed 20 people and injured 30 more at an outdoor Moscow rock concert (“Suicide Bombers,” 2003). The events of September 11, 2001, carried out by unconventional means with devastating results, created the large-scale awareness that public assembly facilities, by their design and purpose, are attractive terrorist targets because of the size of the crowds that gather in them, and the destruction and visibility such a terrorists attack would generate (“Best Practices Planning,” 2002). According to John Pike (2002), director of defense policy think tank Globalsecurity.org, terrorists will soon run out of spectacular targets to hit because these targets will soon be fortified to the point where the terrorists will direct their strikes at less secured targets. Pike stated: “People don’t rob Fort Knox, but they knock over liquor stores every night.” (Clarke, 2002). This statement lends further credibility to the need for further examination of the security protocols in place in secondary market areas to determine if they are equivalent in strength and effectiveness to those in major market areas. In many instances patron, staff, and performer safety can be increased and building liability insurance rates possibly reduced if building managers establish and execute checklists of standard safety procedures for each event (Moxley, 1997).
Best Practices
Reducing risks and potential threats compels venues to implement the best possible practices related to security, as identified by the facility management industry, and have a well trained and highly observant and skilled staff on hand (O’Connor, 2003). Having a properly trained, well supervised staff results in better operations, fewer problems, increased staff morale, less turnover, and guest services that produce higher levels of satisfaction among event attendees (Baugus, 2001).
Venue security in the 21st century will be boosted by technological innovations such as new bomb sensor devices, extensive video capabilities, and archived data of criminals and suspected terrorists that can be displayed and matched against digital photos of people entering public assembly facilities (Enoch & Koss, 2001). Sports facilities are increasing their uses of this cutting-edge security and are relatively ahead of the curve relative to the remainder of corporate America (Iwata, 2002). However, the desire to make facilities safe does not always match resources available to accomplish this task. Therefore, most sports facilities are implementing these advanced security procedures slowly and in phases.
In various European public assembly venues, leisure and entertainment are being directly incorporated into facility grounds to combat organized forms of hooliganism that have plagued the European soccer environment for decades. Unique dining experiences and exclusive shopping venues have created an atmosphere that discourages the criminal activity of the hooligan gangs (Goss et al., 2003). Many facilities in the United States are now providing pre-event entertainment to encourage ticket-holders to arrive earlier to get through security checks in order to prevent long lines at venue entrances at the event starting time (Baugus, 2003). Newer stadia and arenas have utilized crowd management consultants to assist with the design of the facility to reduce security manpower and create environments that encourage fans to come again to the venue (Horck, 2002).
Expanded and more sophisticated guest services are increasingly utilized as important security measures. Patrons engaged in the activities and amenities available at public assembly venues are more manageable and less likely to become violent. Increasingly, commercial interests are participating in the improvement of the hospitality at these facilities and creating environments where incidents of spontaneous and organized terror are less likely to appear (Goss et al., 2003).
Arena Security Systems
Early Efforts
Since the terrorist attacks of September 11, the cost of securing public assembly venues has skyrocketed. Various sports organizations are spending up to the millions of dollars to improve the security according to Howard Safir, a former New York City Police Commissioner, who now works as a security consultant. Officials at all levels of the sporting and entertainment industry realize that another terrorist attack will keep people out of their arenas and stadia, resulting in billions in dollars in lost revenue (Petrecca, 2003).
The worst-case safety or security related scenario for any facility manager is to be unprepared for the unexpected (O’Connor, 2003). As a result, professionals within the public assembly and sports management fields have taken action to develop security protocols and plans to best protect public assembly event patrons and public assembly facilities.
A very basic level of security on which more emphasis is being placed is pre-employment screening, primarily as a result off the increased liability faced by venues, private security companies and event promoters (Hancock, 1998), in an attempt to avoid the debacle of Logan International Airport, an origination point for terrorists on September 11, where over 20 employees were arrested for falsifying or giving false information to get the jobs and security clearances (Madden, 2002). T.J. O’Connor (2003), Vice President of AMSEC, an international risk mitigation firm which specializes in security risk consulting and investigations, stated the best risk reduction practice is to conduct thorough pre-employment screenings and to insist all vendors servicing the building do the same.
The most common security measures of which the public is aware include bag checks, wanding and walk-through metal detectors, although the security measure having the largest impact on increasing safety at public assembly events is increasing the amount of security personnel at these events (Lamberth, 2003). Many security concerns are related to areas of buildings which most building patrons are unlikely to enter. Bio-terrorist threats are seriously considered, and, as a result, closed circuit television cameras monitor and or guards are posted near air intake ducts and water lines supplying the venue (Iwata, 2002). Many building now require card access to office areas, and performers have isolated entrances (Lamberth, 2003). However, all venues are different, and, as such, specific security plans should be designed to fit each buildings strengths and weaknesses.
Industry Recommendations
IAAM’s Safety and Security Task Force established a four-tiered system designed to ascertain threat levels and appropriate matching venue responses that mirror the color-coded security alert system established by the Department of Homeland Security (Herrick, 2003). Table 1 illustrates the correlation between the DHS alert system and venue threat levels (Hancock, 2002).
Table 1: Correlation Between the DHS Alert System and Venue Threat Levels
| Government Rating | Risk Level | Venue Threat | Situation Measures |
|---|---|---|---|
| Severe | 5 | Cancel | Secured |
| High | 4 | Maximum | Government Control |
| Elevated | 3 | Extreme | Restrictive |
| Guarded | 2 | Moderate | Protective |
| Low | 1 | Minimum | Routine |
IAAM recommends that venue managers should develop a security planning process that includes the following steps:
- Assessing risk factors
- Determining threat levels
- Developing and implementing the safety and security plan
Modeled from the security threat conditions issued through the DHS color-coded security advisory system, the IAAM Security Planning Guide for Stadiums/Arenas/Amphitheaters, developed by the SSTF, assists facility managers develop up to four different security plans using over 150 specific security practices. The guide was created as a reference tool to keep facility managers abreast of current and relevant security practices. It is categorized into 20 different security related areas and recommends specific security procedures in each of these areas based on the level of risk associated with the event.
While the DHS color-coded advisory system is based on the likelihood of a terrorist attack with the country, IAAM recommends that venue managers establish contingency plans based on the level of threat relative to each event, which, in some cases, may have little correlation with an organized terror threat. Variables such as the weather, anticipation of rowdy fans, or celebrity attendance may affect the threat level. The IAAM SSTF recommends a fortified system for security planning. A severe warning level by DHS will necessitate the event being canceled and the venue locked down and secured, so the IAAM SSTF recommendations include security levels for events actually taking place.
Level 4 — High Degree of Security Risks
This is the highest level of security risk and may involve national security agencies such as the FBI, Secret Service or other national and international law enforcement and public safety agencies to direct security at the event. Events at this security level are considered a “special event” under the U.S. Homeland Security Act and require strict measures that limit access to the perimeter of the facility prior and during an event. Each person entering the facility is screened for prohibited items at magnetometer checkpoints. Local and state law enforcement officials cannot carry their weapons into the secure area. Events falling under this level of security are generally highly public events of high national significance, attracting thousands of attendees, including high-level government officials and perhaps people from other countries.
Level 3 — Elevated Degree of Security Risk
This is the second highest level of security and may involve national security agencies such as the FBI, Secret Service or other national and international law enforcement and public safety agencies on a limited basis, or to address specific security matters. All or part of the venue has severely limited access. Each attendee and possibly each venue and contract employee will be screened for prohibited items. Events falling under this security level are open to the public with thousands in attendance, including key government officials and perhaps people from other countries and may be televised regionally or nationally. The nature of the event is such that it may attract attendees who normally carry weapons or abuse alcohol and/or other drugs.
Level 2 — Guarded Degree of Security Risk
This is the third highest level of security and may involve regional as well as state and local law enforcement and public safety officials. This level of security may limit access to the facility prior to and during and event. The facility manager controls security measures in the facility. Each attendee is patted down or screened for prohibited items. Events falling under this security level are open to the public and may have government officials, but generally no foreign attendees. These type events have been identified by law enforcement as having no specific security threat outside of the ordinary that normally occurs in the areas in which this event is being held.
Level 1 — Low Security Risk
This level is the minimum necessary for an event. Events falling under this level of security are local or regional in scope and only televised locally, if at all. No government officials are present and outside of normal post-September 11 concerns, poses little or no security threat.
To help facility managers determine the security level to operate, the IAAM SSTF developed a “Decision Tree” to guide these managers through a series of questions with “yes” or “no” answers, based on the criteria of the different security levels, to determine the threat level to their venues (“Best Practices,” 2002). However, IAAM has not yet established a compliance mechanism for the protocols listed in the best practices guides, nor is compliance a requirement for membership. Therefore, the actual application of the best practice protocols is unknown (Jacobs, 2001).
Academic Research
A second initiative relative to safety and security protocols was done by researchers at Springfield College in Springfield, Massachusetts. Based on consultations with the vice presidents of security for the four major professional leagues and extensive reviews of all relevant security data, this research team developed a checklist of best practices for game-day security. After a pilot-tested validation, this checklist was then sent to the athletic directors and university directors of public safety of all of the National Collegiate Athletic Association’s (NCAA) Division I schools within the United States to determine at what level of frequency they used the security measures listed on the checklist. The responses were measured using a five-point Likert-type rating scale (Pantera, Accorsi, Winter, et al, 2003).
The scope of the Springfield College survey included football stadia and university basketball arenas at Division I institutions. The results of the survey identified eight Division I conferences that complied with the proposed security measures at football events at least 75% of the time, and the six conferences meeting the same criteria for basketball events. The researchers concluded the differences in the levels of security and the sheer number of activities in the arena that drive up security costs and make implementation of these security practices economically unfeasible could explain football stadia versus arenas. Additionally, Division I football stadia are often managed and are seen to be more like professional stadia as opposed to a considerable number of Division I college basketball arenas (Pantera, 2003).
The Springfield College study provided useful information with regard to the best security practices recommended by industry professionals to keep facilities and people safe. One of the more interesting findings of the study was the 21 concepts identified as separating the institutions in the top 25% relative to sound security practices from those in the lowest 25%. The correlation separating the most secure facilities from the least secure facilities was calculated for both stadia and arenas. However, the focus of this study centered upon multi-purpose arenas. The separating concepts for arenas are listed in Table 2.
Table 2: Springfield College Security Study Concepts
- Establish central command to coordinate security responses
- Venue lockdown prior to any event
- Bomb sniffing dogs
- Prohibition of all concession deliveries within 90 minutes of an event
- Live security on premises 24/7
- Restricted access to critical areas of the facility
- Implementation of photo identification and zone passes for employees
- Creation of a formal risk management plan
- Implementation of pre-event training programs for all event staff
- Coordination with local and state police agencies
- Preparation of formal evacuation plan
- Awareness of potentially dangerous or explosive facilities nearby
- Implementation of undercover surveillance, with radio equipment dispersed through the building
- No-fly zones over and around the building
- Mobile emergency room vehicle on stand-by
- One crowd observer per 250 people in all sections of the venue
- Security patrols in the parking lot
- Use of periodic broadcast regarding security practices and restricted items to spectators
- Banning carry-in backpacks and other large bags
- Beginning a post-event debriefing for all personnel
One of the more intriguing observations made by the Springfield study research team was that a large percentage of the items separating the respondents with high security scores from those with low security scores were relatively low-cost items. While the research team drew no conclusions as to why the low security cost elements were not being implemented, one of the more obvious answers may possibly be inconvenience, perhaps combined with a relatively low perceived security risk.
Compared with the Best Practices Planning Guide for Stadiums/Arenas/Amphitheaters developed by the IAAM SSTF, the Springfield checklist of 38 security preparations for stadia and arenas has specific guidelines covering all 20 areas identified by the IAAM planning guide. Although perhaps not as detailed, given that the Springfield College checklist does not give specific guidelines relative to varying security threats, this study is very comprehensive in its approach and recommendations relative to security. As pointed out by the vice-president for security at one of the major professional leagues to one of the authors of the Springfield study, the Springfield College security practices essentially detailed the professional league’s security protocols (M. Pantera, personal communication, February 13, 2004).
Methodology
The purpose of this study was to determine if applications of best security practices, as identified in the IAAM Safety/Security Best Practices Planning Guide for Stadiums/Arenas/Amphitheaters, are significantly different in major market locations versus 43 secondary market locations. Quantitative data was collected from professionals in the field of facility management regarding current security practices at their venues to determine any differences in application.
Sample Selection / Description & Data Collection
The sample for this study was taken from public assembly management professionals currently employed at college or university multi-purpose venues who attended the IAAM International Conference in Reno, Nevada, July 23-27, 2004. Administered in conjunction with an educational session presented at this national conference on issues related to the public assembly industry, it was also sent by e-mail to the primary contacts of colleges and universities with IAAM membership not attending the conference. The sample population is limited to IAAM institutional member venues located in the United States with seating capacities of over 3,000 seats. The total sample population consisted of 67 people. Verbal instructions were given prior to the survey’s administration stating that unless multiple buildings with different management teams were found on a single campus, only one representative from each college/university was asked to participate in the study. Those who had participated in the survey at the IAAM International Conference were asked not to participate in the web-based survey in the informational letter attached to the online survey.
The sample, restricted to persons working at college/university multi-purpose venues, included professionals in the field of facility management with various levels of experience and responsibility. At the IAAM International Conference, 53 surveys were administered to the participants with 30 completed surveys being returned. Of the primary institutional member contacts reached via e-mail, 9 responded by returning completed surveys. For the purpose of analysis, the completed survey responses (N=39) were divided into two groups based on the population of the town or city in which the venue at which the respondent is employed was located. One group (n=25) is comprised of venues located in towns or cities with a population of less than 250,000. The second group (n=14) is comprised of venues located in cities with a population of 250,000 or more.
The modified Game Day Security Operations Checklist (see Appendix B) was administered on the same day to all participants as part of an educational session at the 2004 IAAM International Conference. The survey was collected when each participant finished answering it. The instructions were read to each respondent prior to the administration of the instrument, and a brief time for questions and answers was allowed to clarify any confusion. On August 11, 2004, the IAAM Central Office staff sent an e-mail to primary contacts of the 67 institutional members notifying them of the on-line version of the survey after being asked to assist in the data collection for this survey. The same modified version of the Game Day Security Operations checklist was administered via a website to the primary contacts for the 67 institutional members of IAAM having venues with seating capacities over 3,000 seats. Participants’ survey responses were tabulated electronically.
Instrumentation
The instrument used to test for any significant differences in the application of the best security practices as identified by the IAAM Safety and Security Task Force for stadia, arenas, and amphitheaters in major market locations versus secondary market locations was a modified version of the Game Day Security Operations Checklist (2003) used by the Springfield College research team assessing game day security operations at Division I college football and basketball sporting venues (see Appendix A). The Game Day Security Operations Checklist was previously tested for content validation in a pilot study with a number of Division I schools and security experts including the vice presidents of security for the four major professional sports leagues in 2003. The security practices identified by the Springfield College research team included in this instrument were validated by a Delphi study of leading professionals in the security industry as containing elements necessary for a practical and effective security protocol.
The Game Day Security Operations Checklist consists of two parts. The first part asks for demographic information about the respondents’ institutions, including conference affiliation, the security budget, the number of security personnel funded by this budget, the athletic budget, the overall student population, and the average attendance at football and basketball games. The second part lists 38 security concepts, asking the respondents to rate the emphasis their institutions place on each concept for both football and basketball. These 38 security concepts encompass the 20 different security categories of the 150-point IAAM Best Practices Planning Guide for Stadiums/Arenas/Amphitheaters. The ratings are obtained via a Likert-type scale, with responses of “1” indicating “no emphasis” (i.e., this is not part of game-day operations); “2” indicating “moderate emphasis” (i.e., this is featured at 50% of athletic events); “3” indicating “priority” (i.e., this is featured at 75% of athletic events); “4” indicating “we feature this” (i.e., this is a standard part of game-day operations); and “0” indicating “no opinion.”
A modified version of this instrument was used to gather data from the public assembly professionals surveyed for this study (see Appendix B). With this modified version, no demographic information was asked relative to conference affiliation, athletic budgets and attendance at football and basketball games specifically. An additional answer of “Don’t Know” was provided on this study’s instrument on the question which asks for the amounts of the formalized security budgets at the respondents’ institution. In addition to the specific demographic information requested by the Springfield research team, this survey also asked respondents the city/town and population where their venues were located. The respondents were given the choices of “Under 100,000,” “100,000-250,000,” “250,001-500,000,” “500,001- 1,000,000,” and “Over 1,000,000.” A further modification to the Springfield College instrument asked respondents to provide the seating capacity of their venues with the following options given: “Under 3,000,” “3001-7,000,” “7,001-12,000,” “12,001-20,000,” and “Over 20,000.” Finally, respondents were asked to provide the average attendance for all events at their venues with the following options given: “Under 3,000,” “3001-7,000,” “7001-12,000,” “12,001- 20,000,” “Over 20,000,” and “Don’t Know.”
The survey was further modified eliminating the request to rate the emphasis institutions placed on each security concept for football and basketball events since this study is interested in the overall level of preparedness, not the security of a particular sport. As a result, instructions for this item are changed from, “please read the following 38 security concepts and choose one rating according to how much emphasis your institution places on each concept. Please circle only one answer in the football and basketball columns for each concept to ensure survey validity” to, “please read the following 38 security concepts and choose one rating for each concept according to the level of use at your venue. Please circle only one answer for each concept.” The survey format is modified to accommodate this change as well.
Data Analysis
The data gathered from this survey was initially separated into two categories: facilities in cities with over 250,000 people age 12 and over, and facilities in cities or towns with less than 250,000 people age 12 and over. Descriptive statistics were used to determine the mean score for each category on each question. A non-parametric analysis, the Kruskal-Wallis Test, was used to determine if significant differences exist in the responses from each group for each of the 38 checklist items. In addition, a Wilcoxon Signed-Rank Test is used to determine the median of the means for each question for each group and to determine if significant differences were found.
The respondents of this study were asked to rate the applications of the security checklist items in their venues for all events, which may include Level 1 (low) security risk such as tradeshows, beauty pageants, pep rallies, corporate retreats and other similar events. With such low security-risk events (as described in the IAAM Safety and Security Task Force Best Practice Planning Guide for Arenas/Stadiums/Amphitheaters), numerous Game Day Security Checklist items may not be recommended due to their costs and the impracticality of their implementation. Therefore, the variety of the types of events a venue hosts may alter its level of security preparedness needed as reflected in the 38 checklist items implemented. To reduce the likelihood that the conclusions of this study are skewed by the variety of the type of events and venue may host, an additional comparative data analysis was performed for the Game Day Security Operations Checklist measures corresponding with the IAAM Safety and Security Task Force Best Practice Planning Guide for Arenas/Stadiums/Amphitheaters security measures recommended for low risk events.
Further variables were analyzed using other demographic information obtained from the survey responses. In addition to comparative analysis based on the population of the city or town in which the venue is located, comparative analyses were completed based on the formalized institutional security budgets, the number of security personnel funded by this budget, the overall student population the institution, and the average attendance at venue events.
Discussion
Descriptive statistics were used to examine the data submitted by professionals in the public assembly facility management industry. The assumption was made that the data is continuous because it contains answers that are proportioned based on assumptions of what an appropriate response should be. Descriptive Analysis Because the Shapiro-Wilk Test found the data to be non-normally distributed, the means of the responses from the two groups were compared using the Kruskal-Wallis Test (p<.10). Significant differences were found to exist in five instances: the creation of formal risk management plans; the implementation of pre-event training programs for all event staff; the preparation of formal evacuation plans; conducting background checks on all employees, including seasonal and student labor; and the implementation of undercover surveillance teams equipped with radio communications dispersed throughout the venue. The descriptive statistical information on these five occurrences is listed below in Tables 3-7.
Table 3: Mean Comparisons — Q13- Creation of Formal Risk Management Plan
| Group | Count | Sum | Mean | Chi-Square | P-Value |
|---|---|---|---|---|---|
| Major | 14 | 215 | 15.35 | 3.6006 | .058 |
| Secondary | 24 | 526 | 21.92 |
Note: Comparison made using Kruskal-Wallis Test
Table 4: Mean Comparisons — Q15- Implementing Pre-Event Training Program
| Group | Count | Sum | Mean | Chi-Square | P-Value |
|---|---|---|---|---|---|
| Major | 14 | 185 | 13.21 | 8.9758 | .0027 |
| Secondary | 24 | 595 | 23.80 |
Note: Comparison made using Kruskal-Wallis Test
Table 5: Mean Comparisons — Q17- Preparation of Formal Evacuation Plans
| Group | Count | Sum | Mean | Chi-Square | P-Value |
|---|---|---|---|---|---|
| Major | 14 | 228 | 16.25 | 2.93 | .0869 |
| Secondary | 25 | 553 | 22.10 |
Note: Comparison made using Kruskal-Wallis Test
Table 6: Mean Comparisons – Q18- Conducting Background Checks on All Employees
| Group | Count | Sum | Mean | Chi-Square | P-Value |
|---|---|---|---|---|---|
| Major | 14 | 213 | 15.21 | 3.7182 | .0538 |
| Secondary | 24 | 528 | 22.00 |
Note: Comparison made using Kruskal-Wallis Test
Table 7: Mean Comparisons – Q23- Undercover Teams with Radio Equipment throughout the Building
| Group | Count | Sum | Mean | Chi-Square | P-Value |
|---|---|---|---|---|---|
| Major | 14 | 229 | 15.36 | 2.7468 | .0974 |
| Secondary | 25 | 551 | 22.04 |
Note: Comparison made using Kruskal-Wallis Test
The data revealed that in every case where significant differences between the means were found to exist, the mean scores for secondary markets were higher than the mean scores for the major market areas. Additionally, as shown in Table 8, data reveals a trend for the secondary market mean scores to rank higher than the mean scores of the major market areas throughout the survey. A Wilcoxon Signed-Rank Test to determine median differences concluded (82=T<Ttable=281) that the median of the means for the responses from secondary market facilities were higher than the median of the means for responses from major market facilities.
Figure 1: Mean Ranks of Major Market Scores Versus Secondary Market Scores
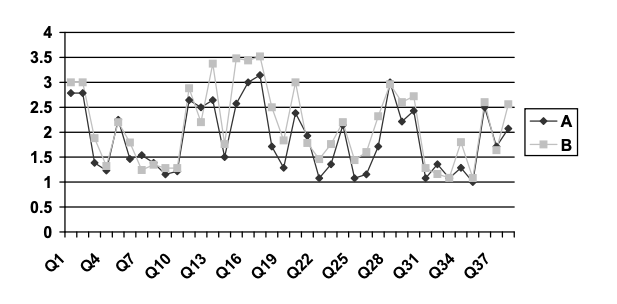
A. Major Market Responses
B. Secondary Market Responses
The information in Figure 1 also reveals that in major market areas 22 of the 38 recommended security checklist items were found to have a mean score of less than 2.0, indicating these security measures are utilized at less than 50% of venue events. Three mean scores were at 3.0 or above, indicating these checklist items are utilized at 75% or more of venue events in this market area. In secondary market locations, 20 of the 38 recommended security checklist items were found to have a mean score of less than 2.0, indicating these security measures are utilized at less than 50% of venue events. Eight mean scores were at 3.0 or above indicating these checklist items are utilized at 75% or more of venue events. Each of the checklist items for each market area in which the mean is 3.00 or higher are listed in Table 8. The checklist items for each market area in which the mean scores were less than 2.00 follow in Table 9.
Table 8: Mean Scores — Security Checklist Items Utilized at 75% or More of Venue Events
| Checklist Item | Market Location |
|---|---|
| Establish Central Command to Coordinate Security Responses | Secondary |
| Venue Lockdown Prior to Event | Secondary |
| Creation of Formal Risk Management Plan | Secondary |
| Implementation of Pre-event Training Programs for All Event Staff | Secondary |
| Coordination with Local and State Policing Agencies | Secondary, Major |
| Preparation of Formal Evacuation Plans | Secondary, Major |
| Awareness of Potentially Dangerous / Explosive Facilities Near Venue | Secondary |
| No Re-entry of Venue for Any Spectator | Secondary, Major |
Table 9: Mean Scores — Security Checklist Items Utilized at Less than 50% of Venue
| Checklist Item | Market Location |
|---|---|
| Patrol of Bomb-Sniffing Dogs | Secondary, Major |
| Installation of Jersey Barriers With a 100-foot Security Perimeter | Secondary, Major |
| Prohibiting Concessions and Other Deliveries Within 90 Minutes of Event | Secondary, Major |
| 24-hour Live Security on Duty | Secondary, Major |
| Installation of Ventilation System to Block Anthrax and Other Hazardous Agents | Secondary, Major |
| Testing Air Quality Prior to Event and Venue Lockdown | Secondary, Major |
| Issuing Holographic Personal I.D. Cards For All Media Clearing Security | Secondary, Major |
| Use of Clear Refuse Bags for 50 Easy Visual Inspection | Secondary, Major |
| Conducting Background Checks Major On All Employees | Major |
| Dictating Cleaning Crews be Escorted BY Security Personnel | Secondary, Major |
| Awareness of Quantities of Anti-dote Secondary, Major Within Region by Central Command Team | Secondary, Major |
| Stockpiling of Drugs to Counter Chemical Secondary, Major And Biological Agents by First Responders On Site | Secondary, Major |
| Implementation of Undercover Surveillance Teams Equipped With Radio Equipment Dispersed Throughout the Building | Secondary, Major |
| Use of Helicopter Patrols of Airspace During an Event | Secondary, Major |
| No Fly Zones Over and Around the Venue | Secondary, Major |
| Mobile Emergency Room Vehicle on Stand-by | Major |
| Implementation of Equipment to Detect Biological, Chemical, and Radioactive Substances | Secondary, Major |
| Utilization of Portable Decontamination Chamber to Handle Threats of Biological, Chemical, and Radioactive Substances | Secondary, Major |
| Use of HazMat Smart Strip for the Detection of Nerve Agents, Cyanide, And Other Chemicals | Secondary, Major |
| Implementation of Periodic Broadcasts Detailing Security Practices and Restricted Items to Spectators | Secondary, Major |
| Implementation of Anti-terrorism Squad Within the Facility | Secondary, Major |
| Implementation of Electronic Ticket Scanning of All Tickets With Detailed record of Season Ticket Holders | Secondary, Major |
The respondents in this study were asked to rate the applications of the security checklist items for all events in their venues which often include Level 1(low) security risk events such as wedding receptions, academic classes, trade shows, beauty pageants, pep rallies, corporate retreats and other similar. Often with these low security risk events, as described in the IAAM Safety and Security Task Force Best Practice Planning Guide for Arenas/Stadiums/ Amphitheaters, a number of the Game Day Security Checklist items may not be recommended. Therefore, the variety of events a venue may host could alter its level of security preparedness for all 38 of the checklist items.
To reduce the likelihood that the conclusions of this study would be skewed by differing varieties of event line-ups at the venues participating in the study, one additional comparative data analysis was done to assess the level of security preparedness at the venues participating in this study. The IAAM Safety and Security Task Force Best Practice Planning Guide for Arenas / Stadiums / Amphitheaters lists a series of security measures to provide a basic protection plan for an event with even the lowest level (Level 1) security risk.
The security measures of this basic protection plan correspond with 13 of the 38 security checklist items listed in the Game Day Security Operations Checklist. In comparing the means for major market venues verses secondary market venues for each of these 13 specific checklist items completed, secondary market venues had higher mean scored higher in 11of the 13 items compared. The 13 security checklist items and the comparative results are shown in Table 10.
Table 10: Checklist Mean Comparison for Basic Security Preparedness for Low Security Risk Events — Major Market Versus Secondary Market Locations
| Checklist Item | Mean Scores | Significant (p<.10) | |
|---|---|---|---|
| Major | Secondary | ||
| Establish Central Command | 2.78 | 3.00 | |
| Prohibition of Deliveries 90 Minutes Before Event | 1.46 | 1.79 | |
| Installation of Ventilation System to Block Anthrax and Other Such Agents | 1.38 | 1.38 | |
| Restrict Critical Areas of the Facility | 2.64 | 2.88 | |
| Creation of Formal Risk Management Plan | 2.64 | 3.37 | Yes |
| Use of Clear Refuse Bag For Visual Inspection | 1.50 | 1.76 | |
| Implementation of Pre-event Training Programs For All Staff | 3.18 | 3.48 | Yes |
| Coordination with Local and State Police | 3.00 | 3.44 | |
| Preparation of Formal Evacuation Plan | 3.14 | 3.52 | Yes |
| No Re-entry by Any Spectator | 3.00 | 2.96 | |
| One Crowd Observer For Every 250 People | 2.21 | 2.60 | |
| Use of Periodic Broadcasts Regarding Safety Policies and Prohibited Items | 1.29 | 1.80 | |
| Banning Carry-in Backpacks and Other Large Bags | 2.50 | 2.60 | |
Conclusions
Hypothesis
The analysis of the data provided sufficient evidence to conclude that the means were significantly different in 5 of the 38 Game Day Security Operations checklist items compared as shown in Table 11 below. Thus, the hypothesis was rejected.
In each of these five instances, the mean scores for the secondary market locations were found to be higher than the mean scores for the major market locations as shown in Table 10. Additionally, the results of the Wilcoxon Signed-Rank Test data analysis provided further evidence to conclude the mean scores for secondary market venues were higher than the mean scores for major market venues in a comparative analysis of the overall survey responses.
Table 11: Checklist Items with Statistically Significant Differences between the Mean
| Checklist Items | Means | |
|---|---|---|
| Secondary | Major | |
| Creation of Formal Risk Management Plans | 3.37 | 2.64 |
| Implementation of Pre-event Training Programs for All Event Staff | 3.48 | 2.57 |
| Preparation of Formal Evacuation Plans | 3.52 | 3.14 |
| Conducting Background Checks on All Employees Including Seasonal and Student Staff | 2.50 | 1.71 |
| Implementation of Undercover Surveillance Teams Equipped With Radio Communication Disbursed Throughout the Venue | 1.76 | 1.36 |
After analyzing data for all responses given by facility management professionals in both major and secondary market locations, one can reasonably conclude that venues located in secondary markets have a higher level of security preparedness than venues in major market areas.
In the study conducted by the Springfield College researchers that assessed game day security preparedness at Division I colleges and universities, a security procedure implemented 75% of the time was a considered to be a successful application, since some checklist items are implemented on a rotating basis at many facilities in response to budget and personnel issues. Given that the Springfield College study measured the implementation of these checklist items for athletic events only (which are events that would normally fall into Level 2 [guarded] or Level 3 [elevated] security risks as defined by the IAAM Safety and Security Task Force), one would expect a widespread and consistent application of the Game Day Security Checklist items because of the increased threat level of these events. Upon the initial examination of the data, even with secondary market venues showing a higher level of security preparedness, it appears that venues in either market size are ill prepared to adequately protect against any serious threat to their patrons, their facilities, or their employees. Data revealed that venues in major market locations applied only 3 of the 38 security checklist items at 75% or more of their events while venues in secondary market locations applied 8 of 38 security checklist items at 75% or more of their venues’ events. This conclusion is further supported by data that indicated major market area venues applied 22 of 38 security checklist items at less than 50% of venue events and secondary market venues applied 20 of 38 security checklist items at less than 50% of their venues’ events.
However, respondents in this study were asked to rate the applications of the security checklist items for all events in the venues which often include Level 1 (low) security risk events such as wedding receptions, academic classes, trade shows, beauty pageants, pep rallies, corporate retreats and other similar events. Based on recommendations by the IAAM Safety and Security Task Force, a number of the Game Day Security Operations Checklist items may be impractical to apply at events with the lowest level of security risk.
To reduce the probability of event variability leading to incorrect conclusions, an additional review of the data was completed to assess the level of security preparedness at venues in major market locations versus secondary market locations. Mean scores for the 13 corresponding Game Day Security Operations checklist items the IAAM Safety and Security Task Force recommends as basic protection for an event with the lowest level (Level 1) security risk were compared. The results of this comparison again showed a higher level of security preparedness by secondary market venues over major market venues.
A review of the Game Day Security Operations checklist items for which secondary market venues applied at 75% or more of their events (see Table 9) indicates that venues management in this market may be adequately providing for the safety and security of their 55 venues, its patrons, and employees in a pre-September 11 environment. Survey data indicate that security at secondary market venues is well coordinated, that the employees have sufficient pre-event training, and that risk management plans are in place to coordinate and give guidelines to the venue employees as how to respond to a variety of situations, become aware of specific building policies, and safely evacuate the building should the need arise. However, data also show venues in secondary markets have made little progress in elevating their security preparedness to prevent organized terrorist attacks against the facility, especially with regard to access to the buildings, air quality inside the facilities, and adequate response measures against chemical and biological attacks. Based on the review of literature, which indicates the focus of future terrorist attacks might be executed upon major market locations, analysis of data relating to secondary market locations indicate what one might expect to find: the venues in this market type are continuing to utilize security measures used prior to September 11 to provide basic security protection with only minor changes or additions to their security preparedness in response to possible new threats.
While the results of this survey regarding the level of security preparedness at secondary market locations met pre-study expectations, levels of security preparedness at major market venues did not. Given the prevalence of media reports on major market areas as possible targets of future terrorist attacks, one might expect the security preparedness of venues in major market locations to have more stringent security measures in place to effectively manage the increasing threat level. At a worse level than secondary market venues, venues operating in major markets locations seem to also be stuck in a pre-September 11 mode in their security preparedness. Of the four instances where major market areas applied a Game Day Security Operations checklist security measure at 75% or more of their venue events, all four were security measures that the IAAM Safety and Security Task Force recommends as necessary for events with the lowest security risk. Similar to secondary market venues, but to a lesser extent, security at venues in major market locations appears to be well coordinated, the employees appear to receive sufficient pre-event training, and risk management plans are in place to coordinate and give guidelines to the venue employees on responding to a variety of situations, become aware of specific building policies, and safely evacuate the building should the need arise. To a greater extent than secondary market venues, venues in major market areas are less than adequately prepared to limit access to their buildings, protect air quality inside the facilities, respond against chemical and biological attacks, and defend attacks against the facilities themselves.
Implications
As indicated in the Introduction and Review of Literature for this study, maintaining adequate security at multi-purpose facilities on college and university campuses is an arduous task. Many colleges or universities are bound by traditions which make change difficult to initiate, especially when opposed by major donors or other influential alumni. The continuing decline of budgets and the limitations of available resources to implement new security procedures, the large number of events at some facilities, along with inflexible capabilities of facility designs of older buildings to accommodate new types of security, all play roles in the inadequacy of facility security at multi-purpose facilities on college and university campuses in the post-September 11 era. However, the failure by college and university administrators to 56 properly secure their multipurpose facilities on their campuses expose these facilities, its patrons, and employees highly vulnerable to catastrophic attacks that may result in facility destruction, serious injuries, and / or many deaths.
Professionals in the public assembly industry are making efforts to ensure that practitioners in the field have the most up-to-date information on the best security protocols available via the utilization of technology, and often provide the information and assistance needed to establish these protocols. However, the issue of whether these security protocols are actually implemented and to what extent needs further examination.
Stadia and arenas filled with large numbers of people will likely remain high on terrorist target lists. As Bruce Hoffman, a Rand Corporation vice president and global security expert opined, the security measures for the 2004 Olympic Games in Athens, Greece, by necessity, assumed a greater magnitude than ever before because they were plum targets for terrorists.
Only a matter of time remains before terrorist groups meaning to harm to the American economy and psyche hit new targets or try again to hit targets where they may have abandoned plans to attack in anticipation of a more favorable time. Therefore, the burden becomes incumbent upon professionals in the public assembly industry to make every effort to provide adequate security protection and create a safe and comfortable environment for fans entering their buildings, regardless of their location and market size.
One area of recommended future research is to determine if the public assembly venues in this study routinely assess risk and threat levels and develop the appropriate contingency responses identified by the IAAM four-tiered alert system, including resources available for security implementation, as well as levels of adherence to identified appropriate responses. The information gathered from this study is useful to facility managers determining which security protocols to implement at their venues and alerting them of potential security breeches that may result in personal injuries to staff and patrons, catastrophic facility damage, and increased liability exposure. Additionally, it may also inform professionals in this field if their security protocols are current with the best practices and technology presently available for use in the industry to maintain safe and secure environments at their venues. Finally, knowledge gained from this study may result in better allocations of resources dedicated to security, increased personal safety, reduced security risks, and associated venue liability.
References
A massive federal makeover. (2002, November 25). CNN.com. Online. Available here.
Altavilla, J. (2002, September 11). The cost of security. The Hartford Courant. Online. Available here.
Baugus, R. V. (2003, September-October). The Louisiana Superdome continues using many of 57 the same security measures it employed while hosting a Super Bowl just months after 9/11. Facility Manager, 30-31.
Baugus, R. V. (2001). Keeping the wheels on: Proper employee training takes on many faces in order to be successful. Facility Manager. Online — No longer available.
Best Practices Planning Guide: Arenas, Stadiums, Amphitheaters. (2002). Center for Venue Management Studies, 1-26.
Cameron, S. (2002, August 28-September 1). Two post-9/11 insurance problems for venues: Getting it and affording it. Sports Business Journal, 5.
Clarke, L. (2002, September 11). Security is measures; Officials struggle with precautions for everyday events. The Washington Post. Online. Available here.
Elrick, M. L. (2002, August 21). The tailgating: Pregame ritual continues in city but fans must stay off the streets. Detroit Free Press. Online — No longer available.
Enoch, M., & Koss, S. (2001). Technology takes center stage in future facilities. Facility Manager. Online — No longer available.
Exec. Order Bi, 13224, 31 C.F.R (2001).
Executive Summary. The National Strategy for Homeland Security. Online — No longer available.
FBI says Al-Qaeda remains top U.S. danger. (2003, September 4). USA Today. Online. Available here.
Fried, G. (1998, March-April). Crowd management: Your facility can be a battle zone. Facility Manager. No longer available.
Goss, B. D., Jubenville, C. J., & MacBeth, J. L. (2003, September-October). Hospitality halts hooliganism: How british soccer facilities utilize revenue streams to undermine troublemakers. Facility Manager, 18-21.
Hancock, D. (1998, May-June). Crowd management: Staff development for t-shirt security. Facility Manager, 27-30.
Hancock, D. (2002, October 28). Best practices protocols: Terrorism response planning for venue managers. IAAM Terrorism Fact Sheet, 1-25.
Herrick, J. (2002, July 26). IAAM releases safety and security planning guide. International Association of Assembly Managers, Inc. Online — No longer available.
Herrick, J. (2003, September-October). The industry benefits from work of IAAM’s safety and security. Facility Manager, 6-8.
Horck, B. V. (2002, October). Playing it safe. Football Business International, 33.
Iwata, E. (2002, March 18). Stadium security gets serious. USA Today. Online — No longer available.
Jacobs, A., Jr. (2001, May 7). Blood sport: Hanging around the hangings. Indianapolis Business Journal, 22, 17.
Justice department contemplates seeking more sweeping powers: Bill would further erode limits on anti-terror powers. (2003, March 28). American Civil Liberties Union. Online — No longer available.
Kennedy, M. (2001, December). Closer scrutiny: In the post-September 11 world, event and activities on school campuses are subject to greater security. American School & University, 74, 48-51.
Lamberth, C. (2003, September-October). Raised awareness: Changing trends in security at sports & entertainment facilities. Facility Manager, 14-17.
Madden, T. D. (2002). Facility pre-employment information and verification, the first level of security defense. Facility Manager. Online. No longer available.
McCaleb, I. C. (2001). Bush announces opening of attacks. CNN.com. Online. Available here.
Meredith, K. (2002). Major lineup present at 2002 AMC. Facility Manager. Online. No longer available.
Moxley, J. (1997, May-June). Establishing standards of performance. Facility Manager. Online — No longer available.
O’Connor, T. J. (2003, September-October). Providing safe and secure venues through risk mitigation. Facility Manager, 26-28.
Palumbo, L. (2003, September). Counterterrorism measures: An essential part of venue security. Public Venue Security. Online — No longer available.
Pantera, M. J., III. (2003, August 18). Planning is key to locking down security. The NCAA News. Online. Available here.
Pantera, M. J., III, Accorsi, R., Winter, C., Gobeille, R., Griveas, S., Queen, D., Insalaco, J., & 59 60 Domanoski, B. (2003, Fall). Best practices for game day security at athletic & sport venues. The Sport Journal, 6. Online. Available here.
Petrecca, L. (2003). Stepping up to the plate: How the sports industry is tackling security in a post-9/11 world. The Graduate School of Journalism at Columbia University. Online — No longer available.
Previous examples of fan violence. (2002, September 20). Sports Illustrated. Online — No longer available.
Romano, J. (2002, November 30). Fans on the field? Forfeit your win. Tampa Bay Times. Online. Available here.
Rovell, D. (2002, September 10). There’s no passing the buck in sports. ESPN.com. Online. Available here.
Rowe, M. R. (1993, April-June). Risky business. Facility Manager. Online — No longer available.
Sports violence in the stands: Is it part of the game? (2001). Horrow Sports Ventures. Online. Available here (PDF).
Suicide bombers strike at concert. (2003, September-October). Facility Manager, 11
The USA patriot act and government actions that threaten our civil liberties. American Civil Liberties Union. Online. Available here (PDF).
Tossed cherry bomb burns boy at baseball game. (2003, September-October). Facility Manager, 11.
Treasury’s O’Neill on Freezing Additional Terrorist Assets. (2001, October 12). U.S. Department of State: International Information Programs. Online. Available here.
Understanding the homeland security advisory system. U.S. Department of Homeland Security. Online. Available here.
USA PATRIOT Act. Online. Available here.
Wheeler, J. (2001, September 17). The Bush doctrine: Hunt down terror. Online. Available here.
JVEM Editorial Board:
Editor: Mark S. Nagel, University of South Carolina
Associate Editor: John M. Grady, University of South Carolina
Consulting Editor: Peter J. Graham, University of South Carolina
JVEM Editorial Review Board:
Rob Ammon, Slippery Rock University
John Benett, Venue Management Association, Asia Pacific Limited
Chris Bigelow, The Bigelow Companies, Inc.
Matt Brown, University of South Carolina
Brad Gessner, San Diego Convention Center
Peter Gruber, Wiener Stadthalle, Austria
Todd Hall, Georgia Southern University
Kim Mahoney, Industry Consultant
Michael Mahoney, California State University at Fresno
Larry Perkins, BC Center Carolina Hurricanes
Jim Riordan, Florida Atlantic University
Frank Roach, University of South Carolina
Philip Rothschild, Missouri State University
Frank Russo, Global Spectrum
Rodney J. Smith, University of Denver
Kenneth C. Teed, The George Washington University
Scott Wysong, University of Dallas