How Ransomware Works
Ransomware is malware that holds your data and privacy hostage, demanding payment in order to regain access. Like most malware, ransomware starts by infecting your computer, most often when you open an infected attachment or click on a malicious link in a phishing email. Once ransomware infects your computer, it encrypts files on your hard drive – possibly even your entire hard drive – or anything else connected to your computer, so you can no longer access your files. It then informs you that the only way you can recover your files is to pay the cybercriminal a ransom (thus the name ransomware).
Sometimes, the criminals also threaten to release your files publicly if you don’t pay the ransom. The criminals may demand payment in the form of untraceable digital currency, such as Bitcoin. If you pay the ransom, the criminals might give you access to your files, but there are no guarantees. Sometimes they will even take your money and still leave your computer infected without you knowing it or keep asking for more money.
How to Protect Yourself from Ransomware
- Back up your computer. Perform frequent backups of your system and other important files, and verify your back ups regularly. If your computer becomes infected with ransomware you can restore your system to its previous state using your backups.
- Store your backups separately. Best practice is to store your backups on a separate device that cannot be accessed from a network, such as on an external hard drive.
- Train your organization. Organizations should ensure that they provide cybersecurity awareness training to their personnel. To improve workforce awareness, an organization can test their personnel with phishing assessments that simulate real-world phishing emails.
- Update and patch your computer. Ensure your applications and operating systems have been updated with the latest patches.
- Use caution with links when entering website addresses.
- Open email attachments with caution. Be wary of opening email attachments, even from senders you think you know, particularly when attachments are compressed files or ZIP.
- Use and maintain preventative software programs.
- Inform yourself!
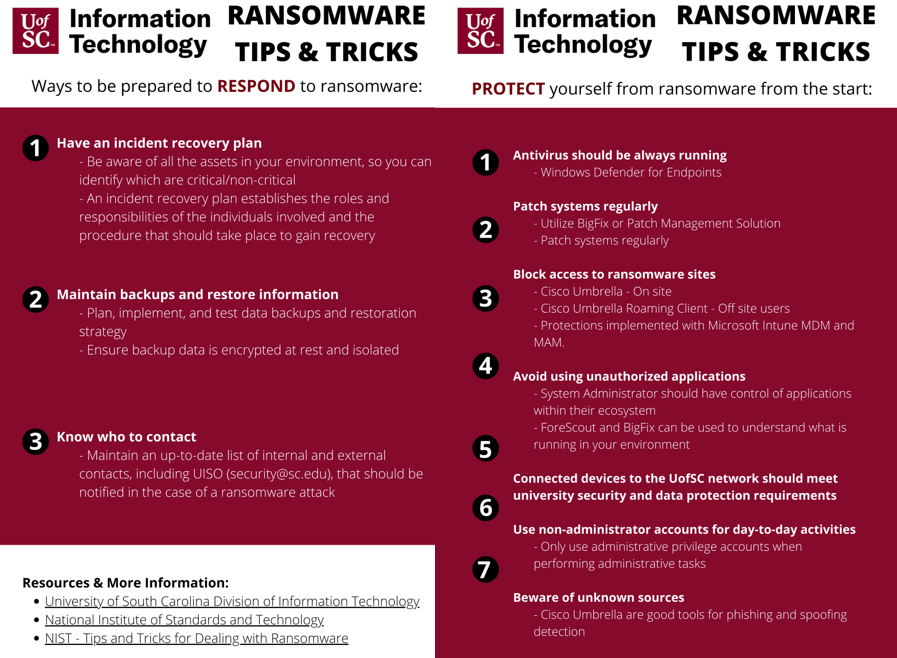
Ways to be prepared to Respond to Ransomware
- Have an incident recovery plan. Be aware of all assets in your environment, so you can identify which are critical/non-critical. An incident response recovery plan establishes the roles and responsibilities of the individuals involved and the procedure that should take place to gain recovery.
- Maintain backups and restore information. Plan, implement, and test data backups and restoration strategy. Ensure backup data is encrypted at rest and isolated.
- Know who to contact. Maintain an up-to-date list of internal and external contacts, including UISO (security@sc.edu), that should be notified in the case of a ransomware attack.